SanerNow VM tool will detect and identify all the vulnerabilities that exist in an account. You can see all the detected vulnerabilities displayed on the All Vulnerabilities page. However, there might be scenarios in which you want VM tool to exclude vulnerabilities from certain devices or groups.
VM tool allows you to exclude vulnerabilities. And you can do this namely at – Account, Group(s), and Device(s) level.
Follow the below mentioned steps on how to exclude vulnerabilities at Account, Group(s), and Device(s) levels.
Step 1: On the VM Dashboard, click on All Vulnerabilities which is located at the top right hand side of the page.
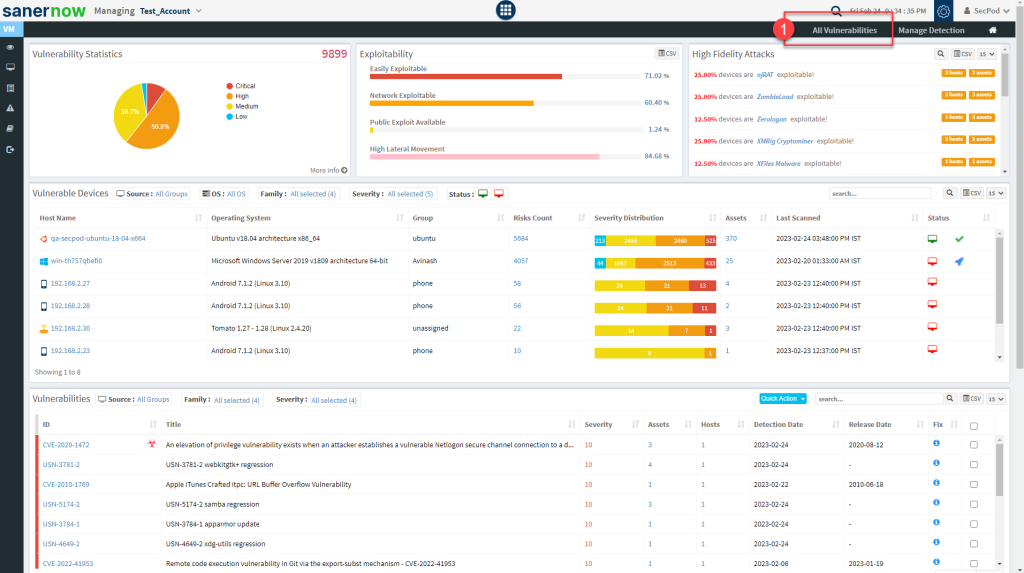
Step 2: You will be directed to the All Vulnerabilities page. Here, you can view all the vulnerabilities found by VM tool.
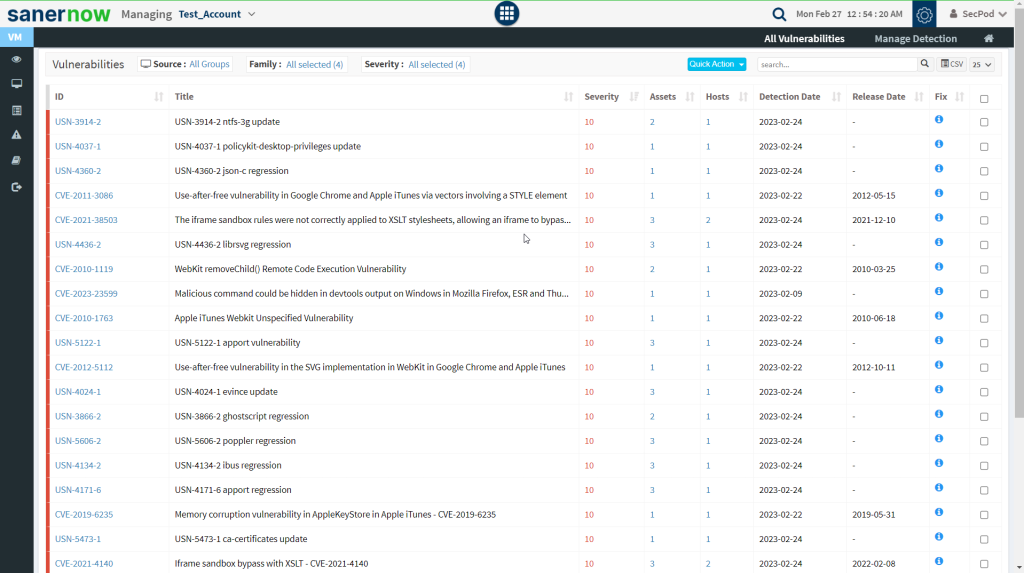
Step 3: Click on the checkboxes displayed towards the right side of the vulnerabilities that you want to exclude. And then click on the Quick Action button.
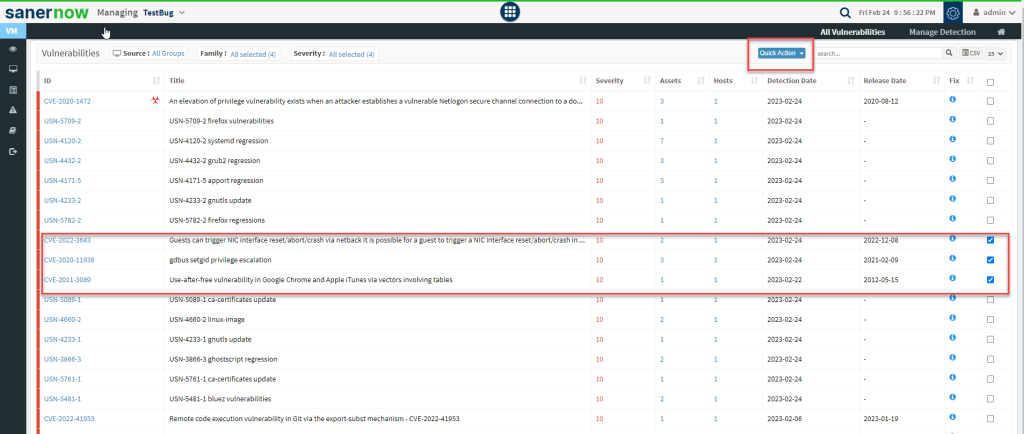
Step 4: You will see two options when you click on the Quick Action button – 1. Exclude and 2. Remediate.
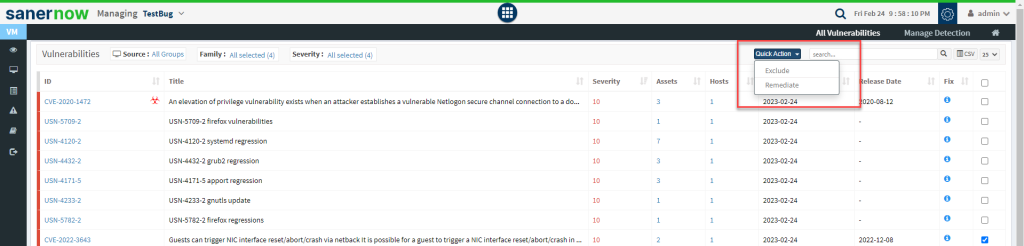
Step 5: Click on Exclude option. You will now be presented with a new pop-up screen.
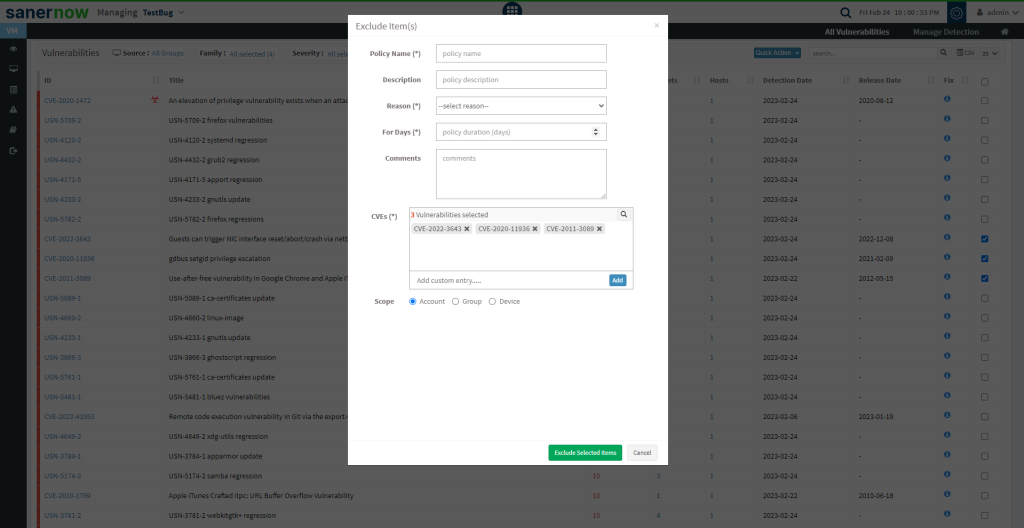
Step 6: You need to fill in information in all the textboxes marked with an asterisk (*). Fill in the required info in the below text boxes.
- Policy Name – Provide a name for the policy you are creating.
- Reason – You need to select the reason you want to exclude the vulnerabilities. Select one of the reasons presented by the drop-down box. The following reasons are available for you to choose.
- False Positive
- Not Applicable
- Risk Accepted
- For Days – Enter the number of days you want VM tool to exclude the vulnerabilities.
- (You can exclude the vulnerability for minimum 1 day and a maximum for 999 days.)
- CVEs – Here, you will see all the vulnerabilities you selected to be excluded. At the same time, you can manually add vulnerabilities to be excluded using the Add button.
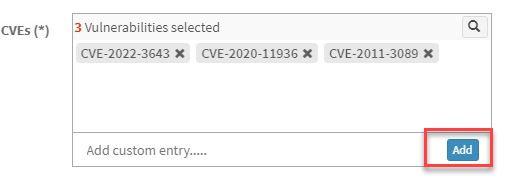
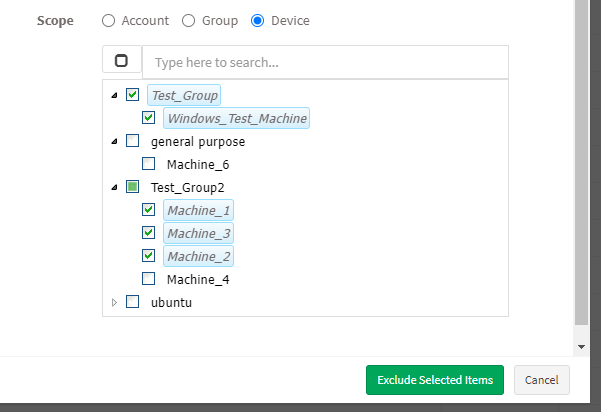
- Scope – You need to select the scope. You can choose between Account, Group, and Device.

- Account – When you select Account, the selected vulnerabilities will be excluded from all the devices that are part of the account till the date specified by you.
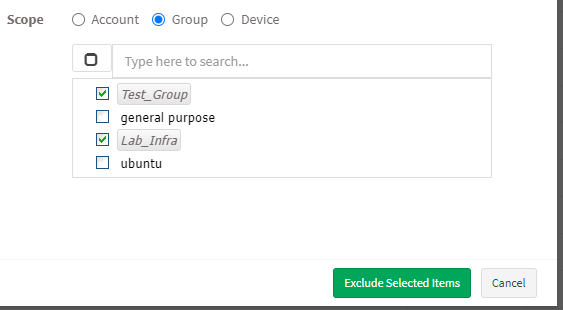
- Group – When you select Group, the selected vulnerabilities will be excluded for all the devices that belong to the selected Group(s) till the date specified by you. (You can select multiple groups)
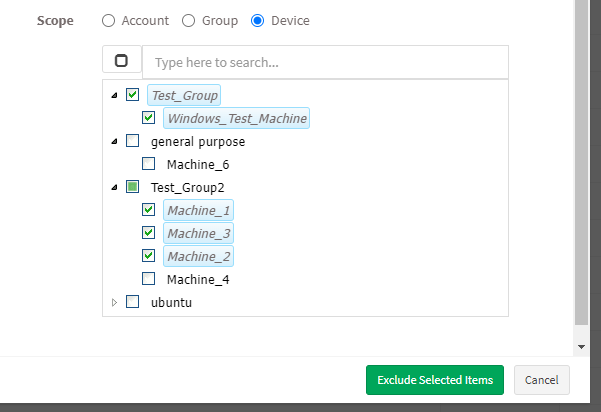
- Device – You can select one or more devices belonging to various groups to exclude the selected vulnerabilities till the time specified by you. You can select multiple devices belonging to various groups to exclude selected vulnerabilities from them.
Step 7: Once you have selected the Scope, click on Exclude Selected Items button. VM tool will exclude the selected vulnerabilities from applicable devices.
How to Exclude Assets in VM tool #
Step 1: On the VM Dashboard, you can find the Top Vulnerable Assets section located at the bottom left corner of the page. All the top vulnerable assets found in the account are listed here.
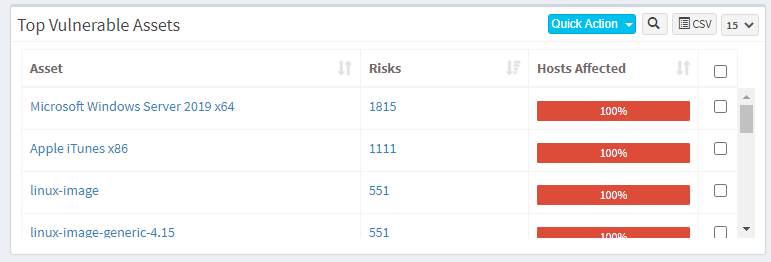
Step 2: You will find the Exclude option when you click on the Quick Action button.
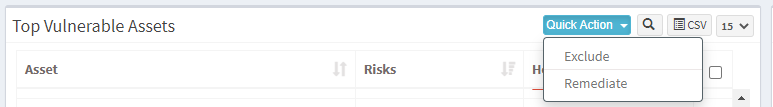
Step 3: You will see two options when you click on the Quick Action button – 1. Exclude and 2. Remediate. Click on Exclude. You will be presented with a new pop-up window.
Step 4: You need to fill in information in all the textboxes marked with an asterisk (*). Fill in the required info in the below text boxes.
- Policy Name – Provide a name for the policy you are creating.
- Reason – You need to select the reason you want to exclude the vulnerabilities. Select one of the reasons presented by the drop-down box. The following reasons are available for you to choose.
- For Days – Enter the number of days you want VM tool to exclude the vulnerabilities.(You can exclude the vulnerability for minimum 1 day and a maximum for 999 days.)
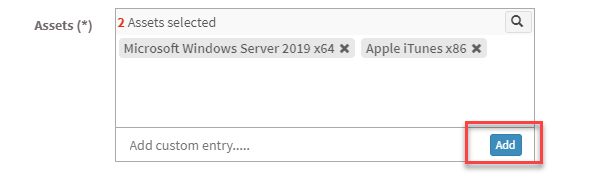
- Assets – Here, you will see all the assets you selected to be excluded. At the same time, you can manually add Assets to be excluded using the Add button.
- You need to select the scope. You can choose between Account, Group, and Device.

- Account – When you select Account, the selected vulnerabilities will be excluded from all the devices that are part of the account till the date specified by you.
- Group – When you select Group, the selected vulnerabilities will be excluded for all the devices that belong to the selected Group(s) till the date specified by you. (You can select multiple groups).
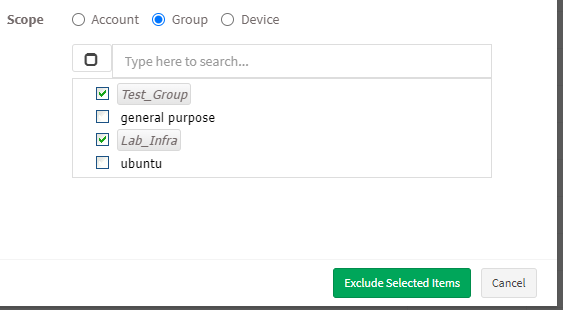
- Device – You can select one or more devices belonging to various groups to exclude the selected vulnerabilities till the time specified by you. You can select multiple devices belonging to various groups to exclude selected vulnerabilities from them.
Step 7: Once you have selected the Scope, click on Exclude Selected Items button. VM tool will create the Exclude policy and exclude the selected assets and all the vulnerabilities belonging to the asset from applicable devices.
Note: In VM tool, you can exclude vulnerabilities in various ways. For instance, you can exclude a vulnerability directly from the vulnerabilities table on the VM Dashboard. However, you must follow the steps mentioned above, irrespective of what page or section you use to exclude a vulnerability.
How to Enable/Disable, Edit and Delete an existing Exclude Policy in VM tool #
Step 1: On the VM Dashboard, click on Manage Detection located at the top right corner of the page.
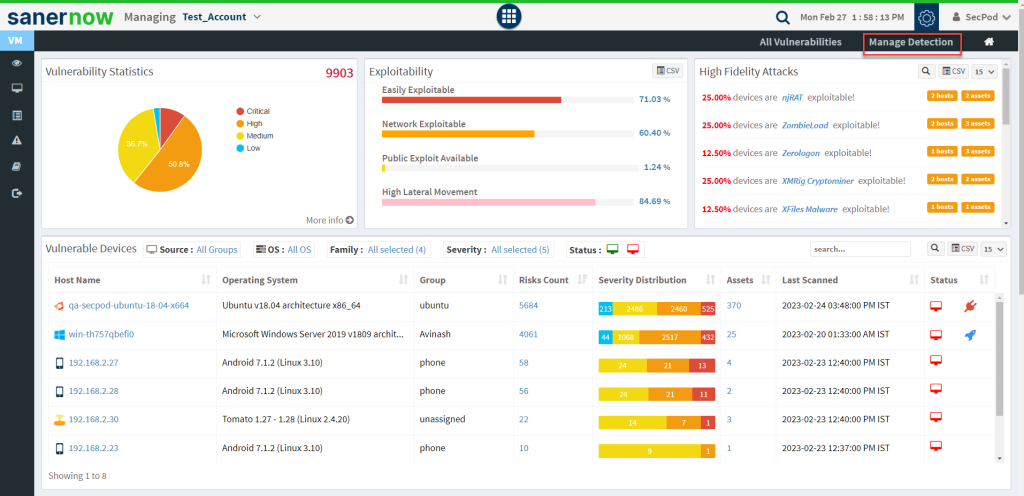
Step 2: You will be presented with a new screen. You can see all the Exclude Policy that exist in the account.
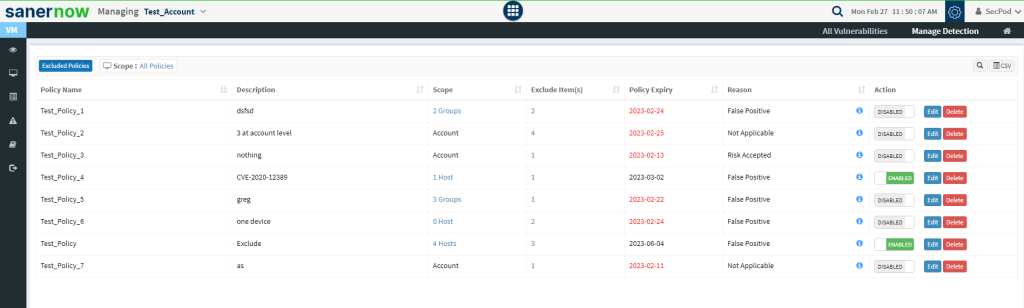
The last column on this page – Action presents you with three buttons namely – a toggle button -Enable /Disable, Edit, and Delete buttons that can be used to control Exclude policies.
| Button | Usage |
 | Using this button, you can enable the Exclude policy. |
 | Using this button, you can disable the Exclude policy. |
 | Using this button, you can edit the Exclude policy. |
| Using this button, you can delete the Exclude policy. |



